The power of tokenization continues to evolve—but not all approaches are equal.
If you’re reading this, you’re likely researching solutions for your organization’s risk, PCI compliance, or privacy problems. As veterans of the payments, cybersecurity, and PCI compliance space, we understand your pain points, and we want to help you learn about technologies that can mitigate or alleviate these issues while empowering your organization to improve its business processes and outcomes.
Today, tokenization has been widely adopted to help companies deal with security and compliance issues such as satisfying privacy regulations, de-identifying nearly any sensitive data type, and helping protect payment data. We want to help you evaluate tokenization solutions based on these capabilities so you can decide which will work best for your specific use case.
Organizations worldwide are deploying tokenization as a data protection control to secure and desensitize their sensitive data. Many security companies and other service providers are beginning to offer their own tokenization services to capitalize on this powerful data protection technology.
However, tokenization capabilities can vary widely between different providers and methods of implementation. Many organizations don’t specialize or focus on tokenization and instead offer it as a secondary service. For example, payment processors or banks may tout their tokenization offerings, but their primary business area is payments—not protecting sensitive data.
Typically, these organizations’ tokenization services aren’t as robust as they could be and are restricted to only transactions occurring on their network. They will only work within their gateways or networks of choice to lock their customers in, almost always charging a hidden fee to return their customers’ raw data. Their solutions often lack support, flexibility, and functionality. Integrations also can be limited, with providers prioritizing convenience and simple implementations over flexibility and comprehensiveness.
In this buyer’s guide, we’ll review the options available to those searching for a tokenization solution and outline the pros and cons of tokenizing your organization’s sensitive data with different providers and technologies. We want to equip you with the necessary information to help you determine how best to collect, secure, store, and access your organization’s sensitive data.
Critical questions for every provider
Every environment is different. There’s no “one size fits all” cookie-cutter approach, so providers should consider the unique requirements of your organization’s technologies and systems. These are the questions you should ask during the procurement process to ensure your concerns are addressed.
Is it compatible with all of my data types?
Which token schemes do you plan to support in the future?
Do you have any data limitations (unstructured, personal, etc.)?
What token schemes are available?
What functionality do your tokens offer?
Do your tokens de-identify data in compliance with my relevant regulatory obligations?
What are the terms and pricing for your data protection platform?
What pricing models do you offer?
What’s the breakdown between capital and operational expenditures?
What are the specific terms of the agreement?
What is your product roadmap?
Does it offer freedom and flexibility in its integrations?
For ecommerce, what acceptance channels do you support?
What are your endpoint capabilities?
Do you offer any additional integrations that can add business value to your solution?
Can it help simplify otherwise disparate and complex security processes?
Does it enable autonomy in vendor and third-party relationships?
Does it preserve the business utility of data for analytics and other valuable insight?
Is it within my budget?
Is your pricing easy to understand?
How will pricing change as our organization grows and our use of the platform increases?
Is the pricing structured in a way that makes sense for our business?
Is it priced competitively within the market?
Is your organization's security tested and validated?
What security controls are in place?
What compliances and assessments do you adhere to/undergo?
Do you have a vendor management program?
Are you utilizing a security framework?
What certifications/validations do you plan to pursue in the future?
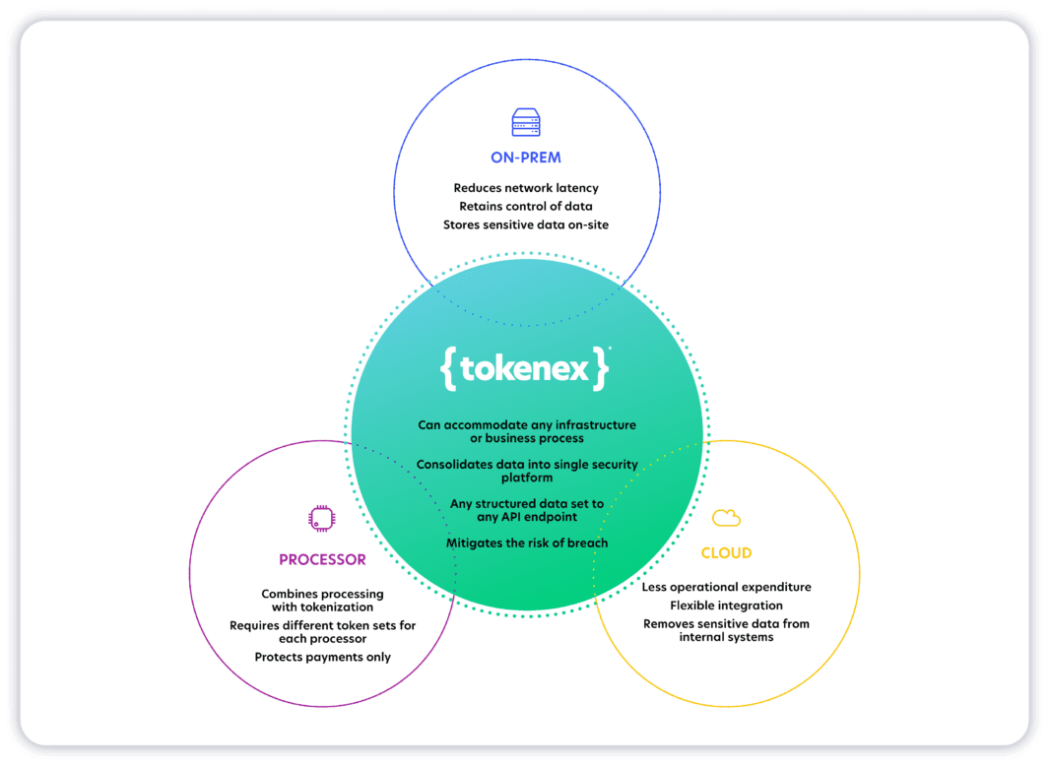
Ultimately, the goal of a tokenization platform is to remove and protect sensitive data from your business systems—whether you’re handling financial information or PCI, personal data or PII, health records or PHI, or even intellectual property. A truly exceptional provider can offer additional benefits, such as consolidating multiple data types from diverse technologies, unifying compliance within a single platform, a modern security architecture that can serve as the central data hub of business operations and other capabilities that facilitate positive business outcomes.
Data protection derives its true value from the business initiatives and functionality it enables. Whether that’s reducing friction, minimizing cost, simplifying systems, or facilitating business processes, the ability to align security with operations to achieve overall organizational success is the key differentiator.
Competitive landscape
Such a provider is not a “transactional” tokenization provider. Instead, it is a robust, enterprise-grade tokenization-as-a-service provider. The tokenization-as-a-service provider enables businesses to drive many powerful outcomes, which we’ll cover below.
Unlike siloed, transactional tokenization, a central token provider spanning customer acquisition channels and different business systems allows companies to realize the value of customer insights across their businesses while removing the risk of holding this sensitive data in its original format.
Autonomy and flexibility in vendor selection
Powerful and agnostic platforms that do not tether tokenization technology to another existing offering (e.g., payment processing) allow companies greater portability and control of their vendors and system designs. As a result, these platforms can be leveraged to create unique, customizable solutions built to satisfy your business needs—not the providers.
A major piece of the compliance puzzle
Sensitive data often runs outside purely transactional lanes, and the ability to interact with and protect data from different origin points across different systems is crucial to scope and risk reduction. Additionally, accepting and protecting multiple data sets is essential for ensuring organization-wide regulatory compliance.
PCI DSS 4.0 Compliance
The PCI DSS 4.0 is the latest version of the global information security framework designed to protect cardholder data. PCI 4.0 aims to help organizations address emerging threats and provide innovative solutions to combat new payment threats.
For many organizations, they spend a significant amount of time and resources on PCI audits. Merchants that store sensitive payment data internally must maintain PCI compliance and deal with the risk of holding this payment data in case of a data breach. To address these PCI compliance problems, organizations may:
Tokenize payment data through their PSP(s)
Tokenize payment data through a tokenization provider
Store sensitive data in their internal systems (and take on additional PCI scope)
Utilize encryption (and take on additional PCI scope)
While PCI compliance is necessary for businesses that accept, process, or transmit cardholder data, it doesn’t have to be complicated, costly, or risky when it comes to handling payment data. A tokenization provider that makes it easy to maintain PCI compliance with lower risks and costs is a worthy investment for the sustainability and success of your organization. The right tokenization provider will help your business:
Minimize PCI scope – spend more time on your business and less time on compliance audits
Reduce costs associated with PCI infrastructure – redeploy money and resources toward more important technology priorities
Avoid storing payment data internally – minimize the impact and costs of a data breach
Avoid the need to create a Cardholder Data Environment (CDE)
Retain the payment data’s value for analysis and tracking while maintaining PCI compliance
Provide the flexibility to work with multiple payment services providers (PSPs)
Tokenization providers do this by:
Replacing sensitive payment data with non-sensitive tokens
Offering flexible, PCI-compliance token formats
Securely accepting payment data from multiple online and in-person channels (e.g., batch file, web, mobile, in-person, 3rd party API, and call centers)
Securely sending payment data to PSPs and third-party partners
Using a fully outsourced cloud tokenization solution
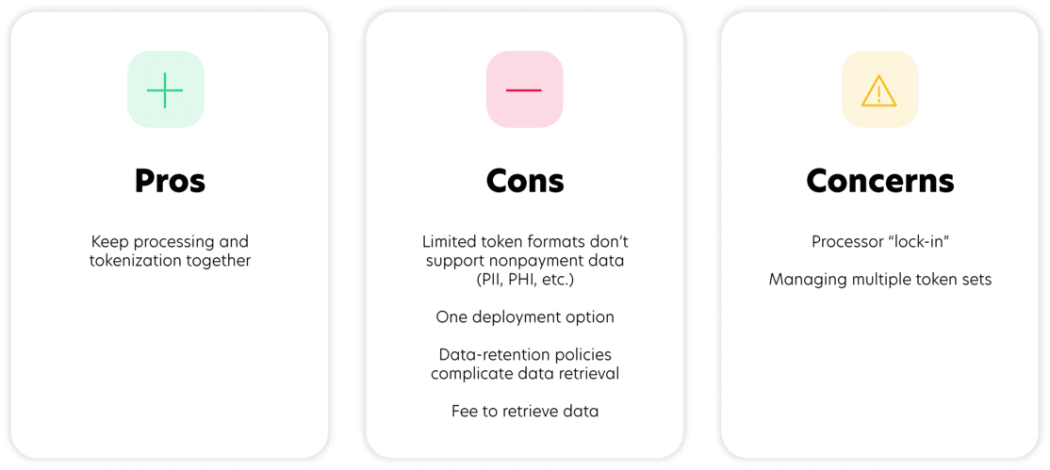
Transactional providers
Third-party payment processors, payment gateways, and acquiring banks commonly offer tokenization services for payment card information. Although using a processor’s additional security services might be convenient, it can often be expensive and difficult to recoup your data once it is tokenized with the payment processor.
Additionally, the amount of PCI scope reduction that can be achieved is limited because the payment card data must traverse the merchant or service provider environment before it reaches the payment processor for tokenization. Lastly, payment processors cannot tokenize other data types like personal and healthcare data, which presents complications and complexity to data protection strategies.
It’s also important to note that payment processors will only protect payment data sent directly to that specific processor. So, if a company wants more than one processor, it will need to manage a token set for each individual processor, increasing complexity around data protection and making customer tracking across these different platforms impossible. This setup can be further complicated if an organization wishes to switch processors, typically requiring the merchant to pay a fee to retrieve its original data.
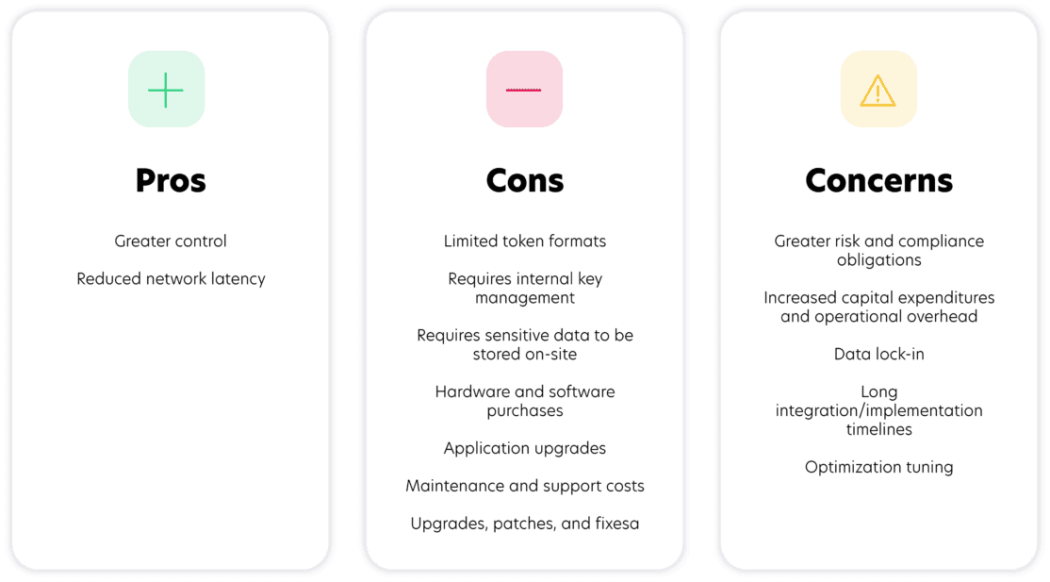
On-premise
Yet another option for data protection is an on-premise solution. On-premise tokenization occurs within an organization’s network and involves purchasing software and hardware. It also requires organizations to keep sensitive data in their environments and shoulder the associated risk, increasing regulatory compliance scope and the potential impact of a data breach.
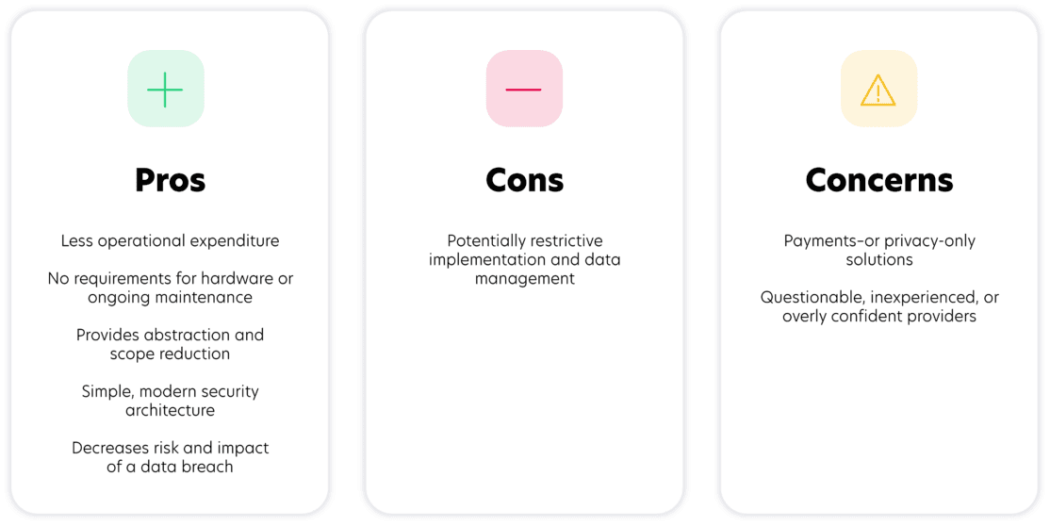
This approach can provide broader data protection capabilities than a siloed, transactional tokenization approach. However, placing security, scope management, and maintenance issues on the shoulders of companies creates complexity and cost, often through a combination of internal staffing and external professional services. The decision around how much security obligations to assume in-house is a significant driver when evaluating on-premise solutions.
Although this model is typically more labor-intensive than other options, it does offer more direct control over implementation and data management. Additionally, reduced latency can be a benefit.
Cloud
Cloud tokenization outsources the tokenization, management, processing, and protection of sensitive data to a third-party cloud platform. As a result, organizations can minimize their compliance scope and maximize risk reduction by tokenizing sensitive data outside of their internal systems. It also improves security by making data inaccessible to thieves and hackers in the event of a breach of a tokenized environment.
Depending on the provider’s implementation capabilities, cloud platforms can tokenize data before it enters an organization’s environment, making it the ideal solution for reducing scope, protecting data, and simplifying compliance. Some providers can also protect multiple data types and data elements originating from diverse systems, although these capabilities vary. Ultimately, it comes down to the experience and expertise of the individual provider.
Essential qualities
Knowledge and experience
Many providers claim to be experts, but not every vendor possesses the knowledge and experience to integrate a tokenization solution that meets your specific needs and promotes your organization’s operational success. True experts should offer the ability—and maintain the credentials—to help you find a solution that enables your desired IT functionality and business operations.
This proficiency should be demonstrated in the provider’s proposed integration, compatibility with your systems, and overall approach: honest, transparent, and confident. Be wary of providers who quickly recite a rehearsed sales pitch or return to a list of talking points rather than listening and responding to your specific questions. An experienced provider should understand your unique needs and take them seriously.
Honesty and transparency
It’s not uncommon for providers to make lofty promises or reckless assurances—such as a pledge of “compliance in X days,” “guaranteed $ return on investment,” or any other questionable claims. These assertions ultimately hurt both the provider and the procurer, leaving the provider unable to fulfill its obligations. You’ll also want to research the provider’s history and ownership. Partnering with an unestablished startup or an organization whose creators aren’t in control of the company can leave you in the lurch if they sell or change hands.
We strongly suggest working only with credible organizations that prioritize your best interests. This means utilizing unbiased third parties and partnering with other trustworthy organizations to ensure your needs and expectations are met. For example, a provider that guarantees one-stop compliance while passing itself off as both vendor and assessor is not only potentially violating the obligations it is claiming to satisfy but also operating with a clear conflict of interest.
In short, the sales process should be focused on finding if you’re a good fit for each other and then building a successful partnership—not misleading or shoehorning the prospect in hopes of another In short, the sales process should focus on finding a good fit for each other and then building a successful partnership—not misleading or shoehorning the prospect in hopes of another quick sale.
Let's chat!
Talk to an IXOPAY security and compliance expert today to learn how we can identify, develop, and deliver a solution that drives positive business outcomes.
Security and risk
It should go without saying, but tokenization providers should first and foremost be concerned with improving security and reducing risk via data protection. Specifically, the provider should be committed to strengthening your security posture and reducing risk to minimize the impact of a breach and simplify the compliance process for any relevant regulatory obligations. This commitment should be verifiable via security and compliance certifications that validate the platform’s efficacy.
Further, it should also be capable of protecting all of your data sets, accepting them via multiple channels, and sending them to any desired endpoint. This should be accomplished by strictly adhering to forward-thinking industry best practices such as Zero Trust and data-centric security principles. Look for the logos below as proof of a provider’s security posture.
Simplicity and flexibility
Ease of implementation and the freedom to integrate with complementary technologies are hallmarks of an effective tokenization solution. Cloud tokenization can simplify the complex by consolidating sensitive data types into a singular data-protection platform, unifying compliance, and streamlining your data environment.
A truly modern security architecture can serve as a central integrator for your organization, allowing you to drive digital transformation, build creative solutions, and achieve an optimized future state for your internal systems. This enables you to integrate with all the third parties you need to interact with your data while simplifying your internal systems and facilitating positive business outcomes.
Rapid time to value
Although an effective tokenization solution should facilitate business agility and offer a nimble implementation process, be wary of any organization boasting streamlined implementations that can be completed in mere days. Realistically, the speed of implementation should be secondary to ensuring it goes smoothly.
A reputable provider should be able to compress implementation times—moving as quickly as you can—but processes for procurement and integration can’t occur overnight. It takes time to evaluate your environment thoroughly, architect an appropriate solution, and complete testing to ensure success at go-live. By doing so, you can benefit from day-one efficacy, even with integrations that include legacy systems, massive volumes of operations, and large data-processing concerns. So although you want a provider to be able to move quickly, make sure it’s not too fast.
Availability and reliability
Data is only as secure as the platform protecting it. Platforms should undergo regular audits and assessments, and providers should be able to share a list of their audit control frameworks and certifications so you can confidently entrust the security of your data to certified industry experts. The platform should also be widely available and consistently reliable. These qualities can be demonstrated via redundancies across multiple data centers in verifiably secure regions and/or countries.
Data centers also should be at least Tier 2 and audited annually by an independent third party. Further, the provider should maintain ownership and complete operational control of all systems within them. Additionally, the data should be continuously synced across data centers to ensure the highest availability standards, with secure platform backups stored with an independent service provider.
These are the things you want to consider when evaluating a provider. Your primary objective should be determining if it can align with your needs and help you meet your goals. Once you have a solid understanding of what type of provider you’re working with, you’ll want to evaluate the specifics of its technology to determine if it’s the right fit for your organization.
Once you have a solid understanding of what type of provider you're working with, you'll want to evaluate the specifics of its technology to determine if it's the right fit for your organization.